Young Researcher Paper Award 2025
🥇Winners
🥇Winners
Print: ISSN 0914-4935
Online: ISSN 2435-0869
Sensors and Materials
is an international peer-reviewed open access journal to provide a forum for researchers working in multidisciplinary fields of sensing technology.
Online: ISSN 2435-0869
Sensors and Materials
is an international peer-reviewed open access journal to provide a forum for researchers working in multidisciplinary fields of sensing technology.
Tweets by Journal_SandM
Sensors and Materials
is covered by Science Citation Index Expanded (Clarivate Analytics), Scopus (Elsevier), and other databases.
Instructions to authors
English 日本語
Instructions for manuscript preparation
English 日本語
Template
English
Publisher
MYU K.K.
Sensors and Materials
1-23-3-303 Sendagi,
Bunkyo-ku, Tokyo 113-0022, Japan
Tel: 81-3-3827-8549
Fax: 81-3-3827-8547
MYU Research, a scientific publisher, seeks a native English-speaking proofreader with a scientific background. B.Sc. or higher degree is desirable. In-office position; work hours negotiable. Call 03-3827-8549 for further information.

MYU Research
(proofreading and recording)

MYU K.K.
(translation service)

The Art of Writing Scientific Papers
(How to write scientific papers)
(Japanese Only)
is covered by Science Citation Index Expanded (Clarivate Analytics), Scopus (Elsevier), and other databases.
Instructions to authors
English 日本語
Instructions for manuscript preparation
English 日本語
Template
English
Publisher
MYU K.K.
Sensors and Materials
1-23-3-303 Sendagi,
Bunkyo-ku, Tokyo 113-0022, Japan
Tel: 81-3-3827-8549
Fax: 81-3-3827-8547
MYU Research, a scientific publisher, seeks a native English-speaking proofreader with a scientific background. B.Sc. or higher degree is desirable. In-office position; work hours negotiable. Call 03-3827-8549 for further information.

MYU Research
(proofreading and recording)

MYU K.K.
(translation service)

The Art of Writing Scientific Papers
(How to write scientific papers)
(Japanese Only)
Sensors and Materials, Volume 36, Number 3(3) (2024)
Copyright(C) MYU K.K.
Copyright(C) MYU K.K.
|
pp. 1035-1046
S&M3579 Research Paper of Special Issue https://doi.org/10.18494/SAM4666 Published: March 25, 2024 Feature Selection for Malicious Detection on Industrial IoT Using Machine Learning [PDF] Hong-Yu Chuang and Ruey-Maw Chen (Received September 20, 2023; Accepted March 12, 2024) Keywords: industrial IoT (IIoT), intrusion detection system, network security, network features
The rapid deployment of IoT devices for enhanced convenience and increased production efficiency has resulted in a significant rise in the potential for cyberattacks. Consequently, the detection of malicious attacks has become a crucial concern in industrial IoT (IIoT) applications. Furthermore, IoT usage is continuously expanding, with new functional IoT devices connecting to the network daily, leading to a substantial increase in network traffic. To address the need for an intrusion detection system (IDS) to identify malicious attacks under a high-traffic condition, a highly efficient IDS is essential. In this study, an IDS based on machine learning (ML) with a reduced set of features on the TON_IoT dataset is employed. The TON_IoT includes telemetry data, operating systems data, and network data for an IoT network. A Pearson correlation coefficient (PCC) was applied to assess the correlations among packet features, and a filtering rule based on the Jamovi software’s frequency table was used to identify the most essential features within the TON_IoT dataset. Finally, the 45 original features were narrowed down to 10 core features for the IDS to effectively detect intrusion activities. To evaluate the detection performance of malicious intrusion activities using the yielded set of 10 core features, we utilized evaluation metrics including accuracy, precision, recall, and F1-score. Four ML techniques, namely, K-Nearest Neighbors, Random Forest, Naïve Bayes, and eXtreme Gradient Boosting, were tested. The experimental results demonstrated that the four ML techniques could detect multiple types of attack with an accuracy exceeding 96% and with a recall rate over 97%, underscoring the effectiveness and efficiency of utilizing the reduced 10 core features for malicious attack detection while maintaining a high level of accuracy.
Corresponding author: Ruey-Maw Chen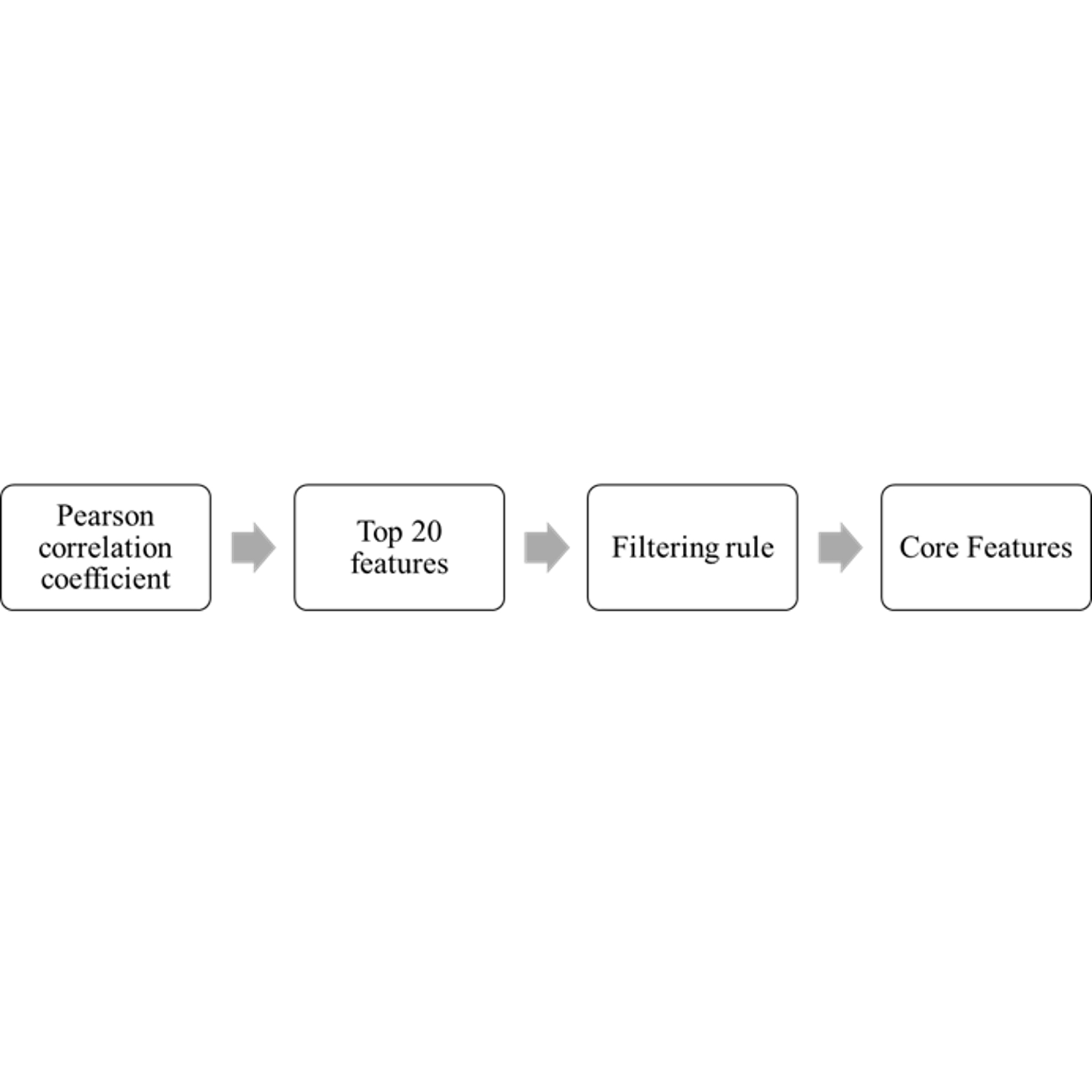  This work is licensed under a Creative Commons Attribution 4.0 International License. Cite this article Hong-Yu Chuang and Ruey-Maw Chen, Feature Selection for Malicious Detection on Industrial IoT Using Machine Learning, Sens. Mater., Vol. 36, No. 3, 2024, p. 1035-1046. |
Forthcoming Regular Issues
Forthcoming Special Issues
Special Issue on Novel Sensors, Materials, and Related Technologies on Artificial Intelligence of Things Applications
Guest editor, Teen-Hang Meen (National Formosa University), Wenbing Zhao (Cleveland State University), and Cheng-Fu Yang (National University of Kaohsiung)
Call for paper
Special Issue on Advanced GeoAI for Smart Cities: Novel Data Modeling with Multi-source Sensor Data
Guest editor, Prof. Changfeng Jing (China University of Geosciences Beijing)
Call for paper
Special Issue on Mobile Computing and Ubiquitous Networking for Smart Society
Guest editor, Akira Uchiyama (The University of Osaka) and Jaehoon Paul Jeong (Sungkyunkwan University)
Call for paper
Special Issue on Advanced Materials and Technologies for Sensor and Artificial- Intelligence-of-Things Applications (Selected Papers from ICASI 2026)
Guest editor, Sheng-Joue Young (National Yunlin University of Science and Technology)
Conference website
Call for paper
Special Issue on Innovations in Multimodal Sensing for Intelligent Devices, Systems, and Applications (submission closed)
Guest editor, Jiahui Yu (Research scientist, Zhejiang University), Kairu Li (Professor, Shenyang University of Technology), Yinfeng Fang (Professor, Hangzhou Dianzi University), Chin Wei Hong (Professor, Tokyo Metropolitan University), Zhiqiang Zhang (Professor, University of Leeds)
Call for paper
Special Issue on Biosensing Devices
Guest editor, Kiyotaka Sasagawa (Nara Institute of Science and Technology)
Call for paper
-
For more information of Special Issues (click here)
-
Special Issue on Multisource Sensors for Geographic Spatiotemporal Analysis and Social Sensing Technology Part 5
- Accepted papers (click here)
- High-precision Autonomous Driving Map Quality Inspection Indicator System and Evaluation Method
Chengcheng Li, Ming Dong, Hongli Li, Xunwen Yu, Yongxuan Liu, and Chong Zhang
- High-precision Autonomous Driving Map Quality Inspection Indicator System and Evaluation Method
- Accepted papers (click here)
- Voltage Reflex and Equalization Charger for Series-connected Batteries
Cheng-Tao Tsai and Jia-Wei Lin
- Voltage Reflex and Equalization Charger for Series-connected Batteries
- Accepted papers (click here)
- Design and Development of a Fuzzy-logic-based Long-range Aquaculture System
Sheng-Tao Chen and Tai-I Chou
- Design and Development of a Fuzzy-logic-based Long-range Aquaculture System
Guest editor, Prof. Bogang Yang (Beijing Institute of Surveying and Mapping) and Prof. Xiang Lei Liu (Beijing University of Civil Engineering and Architecture)
Special Issue on Materials, Devices, Circuits, and Analytical Methods for Various Sensors (Selected Papers from ICSEVEN 2025)
Guest editor, Chien-Jung Huang (National University of Kaohsiung), Mu-Chun Wang (Minghsin University of Science and Technology), Shih-Hung Lin (Chung Shan Medical University), Ja-Hao Chen (Feng Chia University)
Conference website
Call for paper
Special Issue on Sensing and Data Analysis Technologies for Living Environment, Health Care, Production Management, and Engineering/Science Education Applications (2025)
Guest editor, Chien-Jung Huang (National University of Kaohsiung), Rey-Chue Hwang (I-Shou University), Ja-Hao Chen (Feng Chia University), Ba-Son Nguyen (Lac Hong University)
Call for paper
Special Issue on Advances in Sensors and Computational Intelligence for Industrial Applications
Guest editor, Chih-Hsien Hsia (National Ilan University)
Call for paper
Special Issue on AI-driven Sustainable Sensor Materials, Processes, and Circular Economy Applications
Guest editor, Shih-Chen Shi (National Cheng Kung University) and Tao-Hsing Chen (National Kaohsiung University of Science and Technology)
Call for paper
Special Issue on Intelligent Sensing and AI-driven Optimization for Sustainable Smart Manufacturing
Guest editor, Cheng-Chi Wang (National Sun Yat-sen University)
Call for paper
- Accepted papers (click here)
Copyright(C) MYU K.K. All Rights Reserved.
